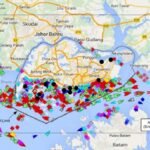
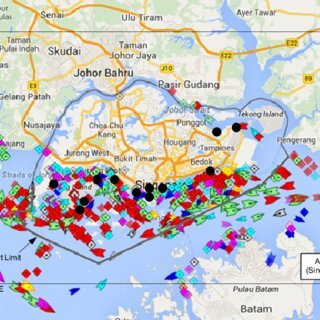
Cyber threat intelligence has evolved beyond traditional indicators of compromise. Modern adversaries operate across underground forums, encrypted marketplaces, and deep web ecosystems where stolen credentials and access data are traded at scale. One of the most significant developments in recent years…